From unforeseen challenges to unexpected opportunities, we keep your organization moving forward with unwavering resilience.

Comprehensive business continuity planning is a proactive and strategic approach to identify potential risks and threats that could disrupt business operations and developing a detailed plan to ensure the continuity of critical business functions during and after an unexpected event. It involves assessing the potential impact of various threats, identifying essential business functions, and developing strategies and procedures to minimize disruption and restore operations as quickly as possible.
Our goal is to provide your business with the tools and expertise to prepare, respond, and recover from unexpected events by developing and implementing a comprehensive business continuity plan that ensures uninterrupted operations and minimizes the impact of potential disruptions.
A comprehensive business continuity plan covers all aspects of a business, including IT infrastructure, supply chain management, workforce management, communication, and financial planning. It is an ongoing process that requires regular testing, updating, and review to ensure it remains effective and relevant to the changing business environment.

Rather than using a one-size-fits-all approach, we customize solutions that are specific to each client's unique needs and requirements.

Conduct a comprehensive risk assessment that identifies potential threats and vulnerabilities and determines their potential impact on business and IT operations.

We foster collaboration between departments and stakeholders to create a culture of resilience, where everyone is invested in the success of the business continuity program initiative.

Continuously test and refine the plan to ensure it remains effective and relevant to the changing business environment.

Utilize technology and automation tools to improve response times, minimize disruption, and increase efficiency during an emergency.

Train employees on their roles and responsibilities during an emergency to ensure a swift and effective response. Employees and stakeholders will know what to do before, during, and after an emergency and most importantly, when to activate their continuity plan.

Are you unsure whether your business continuity program meets regulatory compliance and standards? A Business Continuity Maturity Assessment is an important tool for organizations to evaluate and improve their readiness to respond to and recover from disruptions. It helps organizations identify weaknesses, prioritize investments, ensure compliance, increase customer confidence, and reduce downtime.
The business continuity maturity assessment is broken into six levels of maturity, which are assessed within seven corporate competencies, and an eighth section that focuses on business continuity program content. The six levels of maturity are:


A Business Continuity Assessment provides organizations with a structured approach to identify risks, strengthen resilience, ensure compliance, enhance communication, minimize financial impact, and boost customer and stakeholder confidence. By investing in business continuity assessment, organizations can proactively prepare for disruptions, safeguard their operations, and maintain their competitive edge.

A Business Continuity Maturity Assessment helps an organization identify areas of weakness in their continuity plan. This can include gaps in resources, communication, or response times. By identifying these weaknesses, the organization can take steps to address them and improve their overall resilience.

An assessment can help an organization prioritize investments in business continuity planning. This includes investing in technology, training, and personnel to ensure that the organization is prepared to respond to any disruptions.

Many industries have regulations that require businesses to have a continuity plan in place. An assessment can help organizations ensure that their plan meets regulatory requirements and is up-to-date.

By having a robust continuity plan in place, an organization can increase customer confidence. Customers want to know that the businesses they rely on can continue to operate even in the face of disruption.

By identifying weaknesses in the continuity plan, an organization can take steps to reduce downtime in the event of a disruption. This can help the organization minimize the impact of a disruption on its operations and its bottom line
REMVER approach to the business impact analysis involves identifying critical business functions and dependencies, and quantifying the potential financial and operational impact of disruptions to prioritize recovery efforts.
The Business Impact Analysis (BIA) is a critical component of any business continuity planning effort. It helps organizations to identify their critical business functions, assess the potential impact of disruptions, and develop effective recovery strategies to minimize the impact of disruptions on their operations.
The first step is to clearly define the scope of the BIA, including the business units, processes, and systems that will be included in the analysis. You should also define the objectives of the BIA, such as identifying critical business functions and determining the potential impact of disruptions on these functions.
Based on the potential impacts and RTOs, develop recovery strategies for each critical business function. These strategies may include backup systems, alternative processes, and procedures for communication and coordination.
Identify the critical business functions that are necessary to maintain operations. This includes identifying the dependencies between business units and processes.
Test the BIA by conducting a scenario-based exercise to validate the assumptions made during the BIA. This will help to identify any gaps in the recovery strategies and improve the effectiveness of the plan.
Identify the potential impacts of disruptions on each critical business function. This includes identifying the financial, operational, reputational, and legal impacts of disruptions.
Update the BIA on a regular basis to reflect changes in the business environment, such as new processes, systems, or dependencies.
The RTOs represent the maximum allowable downtime for each critical business function. Determine the RTOs based on the potential impacts of disruptions and the business requirements for each function.

With our Business Continuity and Disaster Recovery (BC/DR) solutions, we help you catalog your organization’s mission-critical processes and systems and develop detailed business continuity and disaster recovery plans so you can protect your organization from disruption.


Catalog your organization’s mission-critical processes and systems and develop detailed business continuity and disaster recovery plans so you can protect your organization from disruption.

Automate the process of activating business continuity, disaster recovery and crisis plans to facilitate a coordinated and aligned response to crisis events. Archer Crisis Management helps you coordinate information, priorities, and objectives among business continuity, disaster recovery, and crisis teams.

Consistent, coordinated, and automated approach to performing risk assessments and documenting and testing business continuity and IT disaster recovery plans for your business processes, locations, IT applications and infrastructure, and information assets.

Centralize and streamline the tracking, workflow, and resolution of various incidents before they disrupt your business. You can also categorize incidents to quickly evaluate their criticality and determine appropriate response procedures, assign response team members, and much more.
At REMVER, we are dedicated to helping businesses prepare for, respond to, and recover from emergencies.
Before an emergency, we work with businesses to develop robust emergency response plans that cover a range of potential scenarios. We also help companies identify potential vulnerabilities and develop strategies to mitigate risks.
During an emergency, our team provides support to businesses in real time. We offer guidance on how to activate emergency plans, coordinate with emergency responders, and communicate with stakeholders. We also help businesses assess the situation and make critical decisions that prioritize the safety of employees and customers.
After an emergency, we assist businesses in recovery efforts by providing support for damage assessment, insurance claims, and business continuity planning. We work closely with companies to evaluate the effectiveness of their emergency response plans and identify areas for improvement.

We understand that every emergency is unique and requires a tailored response. That's why our team is highly agile and able to adapt quickly to changing circumstances. We prioritize rapid response times and effective communication to ensure that our client's needs are met in a timely and efficient manner.

We believe that collaboration is key to success in any emergency. That's why we work closely with our clients to understand their specific needs and develop customized solutions that are tailored to their requirements. We also collaborate with other stakeholders, such as law enforcement and regulatory bodies, to ensure that our response is comprehensive and effective.

We are committed to staying at the forefront of the latest technologies and best practices in incident response. This allows us to provide our clients with innovative and effective solutions that are designed to meet their unique needs. We also believe in continuously learning and improving our processes to ensure that we are always delivering the highest level of service to our clients.

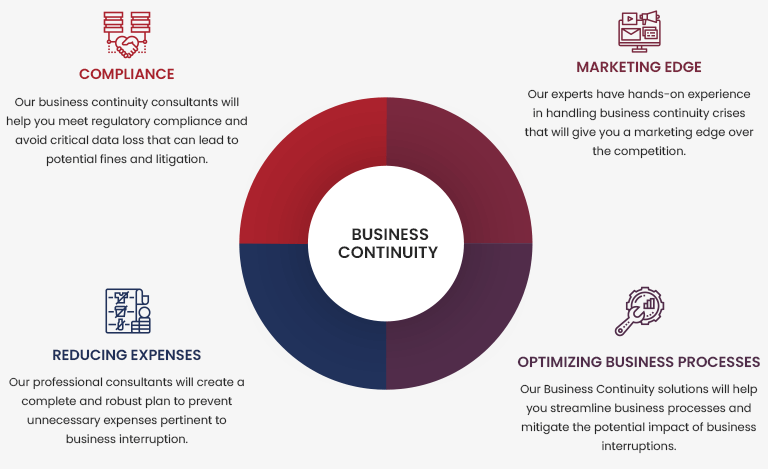
Implementing a comprehensive business continuity program can help minimize the impact of disruptive events, ensure timely recovery, and maintain critical business operations. In addition, a business continuity program is critical for organizations to ensure their resilience and preparedness for any potential disruptions to their operations. It can help to protect their reputation, comply with regulatory requirements, increase customer confidence, and minimize the financial impact of disruptions.
Minimizes Downtime: A business continuity program helps organizations to minimize downtime and reduce the impact of a disruption on their operations. This means that the organization can continue to provide services or products to its customers even during a crisis, minimizing financial losses and preserving its reputation.
Protects Business Reputation: A business continuity program helps organizations to protect their reputation by minimizing the impact of disruptions on their operations. This is particularly important for organizations that rely on customer trust and loyalty to maintain their business.
Improves Regulatory Compliance: Many industries have regulations that require businesses to have a business continuity plan in place. Having a business continuity program ensures that organizations meet these regulatory requirements and can avoid costly fines and penalties.
Increases Customer Confidence: A business continuity program can increase customer confidence by demonstrating that the organization is prepared to respond to disruptions and protect the interests of its customers. This can lead to increased loyalty and trust among customers.
Enhances Organizational Resilience: A business continuity program enhances organizational resilience by identifying potential risks and developing strategies to mitigate them. This means that the organization can quickly adapt to changes in the business environment and continue to provide services or products to its customers.
Reduces Financial Losses: A business continuity program can help organizations to reduce financial losses by minimizing the impact of disruptions on their operations. This includes lost revenue, increased expenses, and damage to equipment and facilities.
Improves Employee Safety: A business continuity program ensures that employees are prepared and trained to respond to emergencies, protecting their safety and well-being. This also helps to maintain business continuity by ensuring that employees can continue to work even during a crisis.
As a professional consulting firm, we pride ourselves on our unique approach to managing threats. Our methodology involves conducting a thorough risk assessment to identify the most critical risks facing our clients. We then tailor our solutions to meet the specific needs of each client, based on their unique risk profile. Our solutions may involve implementing new security measures, developing emergency response plans, or providing training and education to staff. We also provide ongoing monitoring and assessment to ensure that risks are identified and addressed in a timely manner.
Our collaborative approach involves working closely with stakeholders across the organization to ensure that everyone is aware of the risks and can work together to mitigate them. Our goal is to provide our clients with the tools and support they need to effectively manage and mitigate threats, protecting their business and minimizing risk. By leveraging our expertise and experience, we help our clients navigate the increasingly complex threat landscape, enabling them to focus on their core business objectives with confidence.

Subscribe to newsletters, articles, blogs, webcasts, events, and more delivered straight to your inbox.
Subscribe to newsletters, articles, blogs, webcasts, events, and more delivered straight to your inbox.
Fill in the form below.
Fill in the form below.
Fill in the form below.
Fill in the form below.
Fill in the form below.
Fill in the form below.
Fill in the form below.
Fill in the form below.
Fill in the form below.
Fill in the form below.
Fill in the form below.

Experience the power of Technology: Swiftly navigate business disruptions with REMVER Consulting’s tailored-made solutions.